0x0G Google CTF 2020 (todo)
Hi everyone today I’m writing about android reversing challenge from google 0x0G CTF 2020 so let’s start.
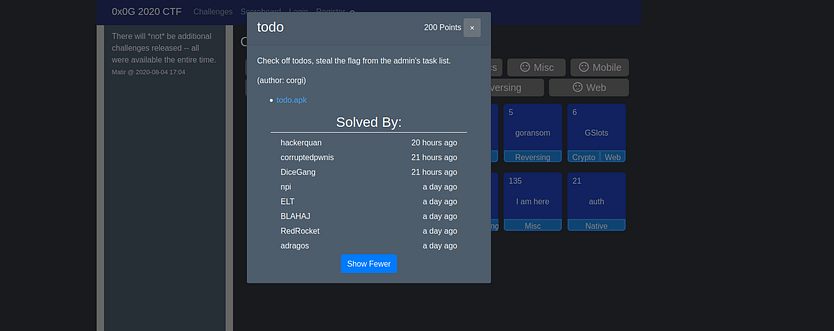
this challenge had solved by only 8 teams. We got an apk file and we have to steal the flag from admin as per the description : “Check off todos, steal the flag from the admin’s task list.” so I thought that there might be some kind of authentication vulnerability that will give us admin access ????
so I installed todo.apk on my android device in order to capture request in burp suite and I found that they were using firebase authentication and database then I realized that authentication vulnerability was not possible so I downloaded the todo.apk on my system to review the source code so I decompiled the apk to get the source code using jadx and I got the source code of todo.apk
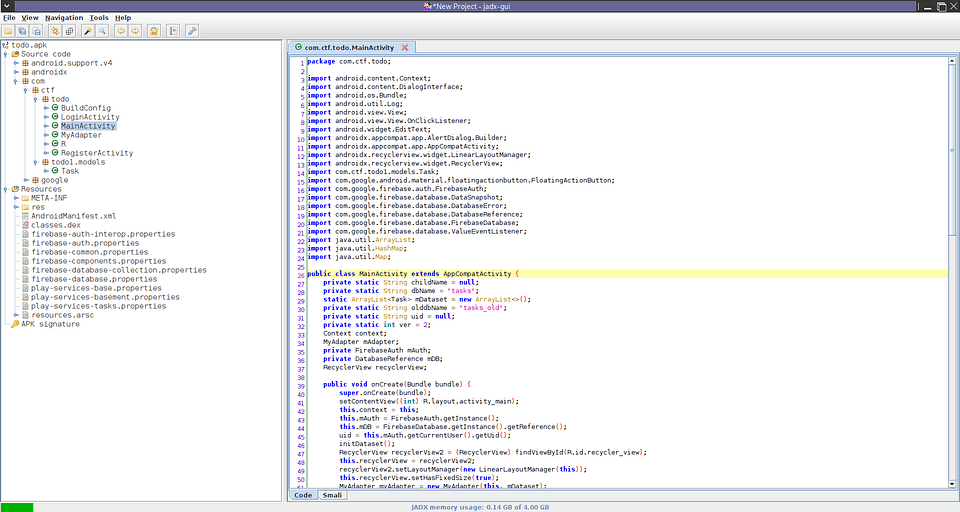
Now there was no obfuscation it means we can easily reverse this application so before reversing it I opened the strings.xml to find the firebase database URL to check that security rules was on place or not.
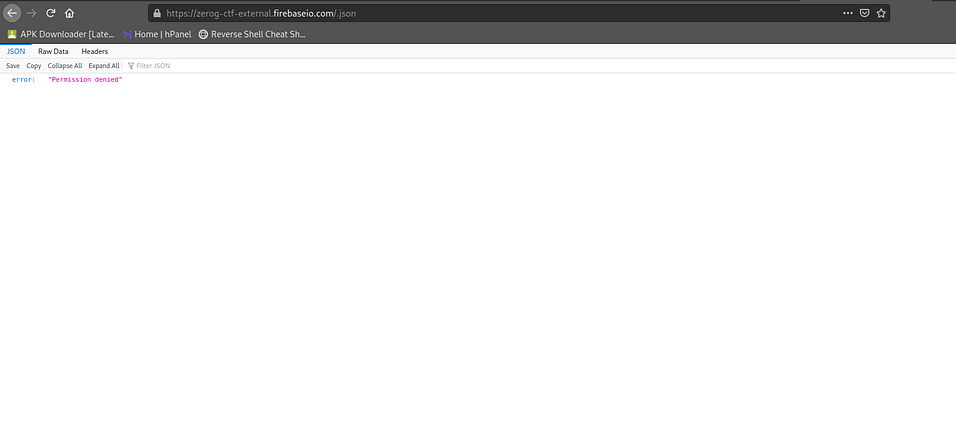
and firebase database was secure that’s why we can not get the flag directly so now lets understand the code. I cloned the code in android studio and now I can easily test this application.
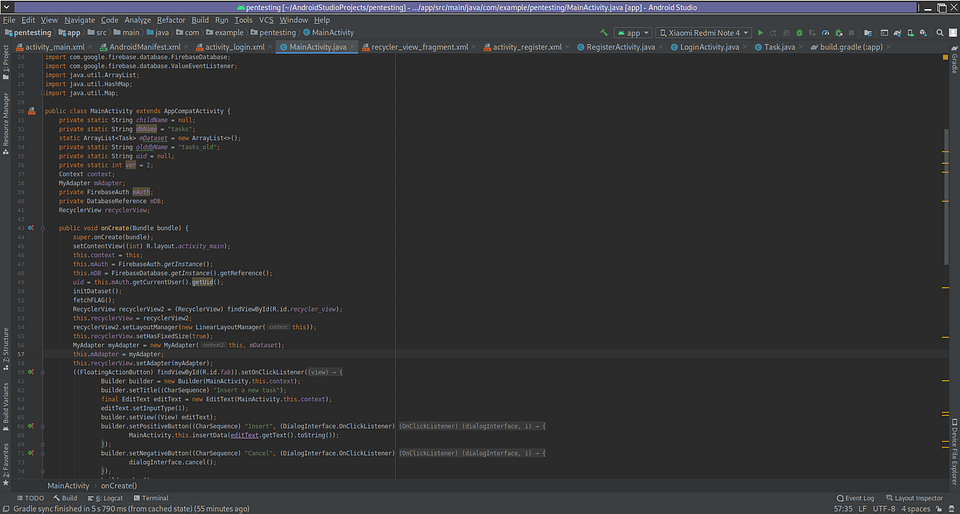
Now I asked two question from myself that :-
- Is their any way to get the unique user id of the admin?
- Can we do something with login functionality to get into admin account without knowing username & password ?
after workaround I found answers for both questions:-
- Is their any way to get the unique user id of the admin? – YES 🙂
- Can we do something with login functionality to get into admin account without knowing username & password ? – NO
Yes we can get unique user id of the admin 🙂 . We can also get flag by adding few lines of code.
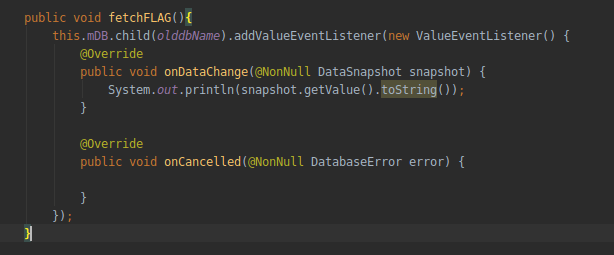
we added this function fetchFLAG() to fetch all the tasks added by users in our database so first I tried it with database named as tasks and I got an error permission denied then I tried it with database named as tasks_old and I was able to fetch all the tasks added by users and I got the uuid (“2qztPFVDKlTkfxvizhahmNpNkQx10G“) of admin’s account and flag 🙂
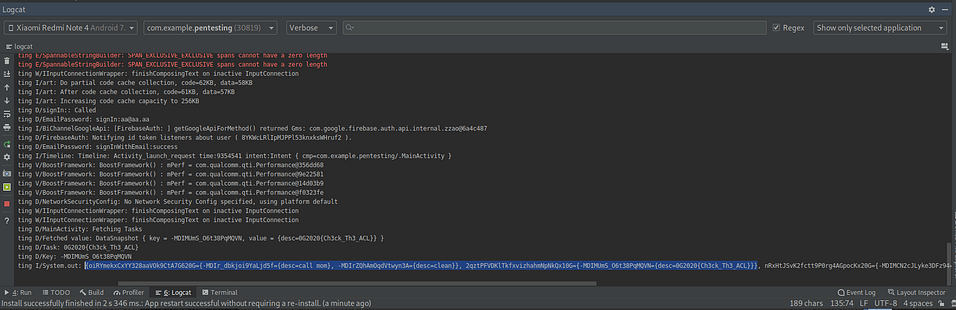
- FLAG => 0G2020{Ch3ck_Th3_ACL}